Chapter 3 Forensic Analysis Tools for Windows Systems
In Chapter 3 we discussed approaches to conducting a forensic examination of Windows systems for malware and associated artifacts. There are a number of forensic analysis tools that you should be aware of and familiar with. In this section, we explore these tool alternatives, often demonstrating their functionality. This section can also simply be used as a “tool quick reference” or “cheat sheet,” as there will inevitably be an instance during an investigation where having an additional tool that is useful for a particular function would be beneficial, but while responding in the field you will have little time to conduct research for or regarding the tool(s). It is important to perform your own testing and validation of these tools to ensure that they work as expected in your environment and for your specific needs.
| Mounting Forensic Duplicates |
| Name: FTK Imager |
| Page Reference: 159 |
| Author/Distributor: AccessData |
| Available From: http://www.accessdata.com |
| Description: Although FTK Imager a free tool that is primarily used to create and convert forensic duplicates of storage media and files, it has the capability to present a forensic duplicate as a volume and hard drive attached to the computer. This feature of FTK Imager is depicted below and can be useful for running tools that cannot process a forensic duplicate directly and require a mounted file system. |
| Name: MountImage Pro |
| Page Reference: 158 |
| Author/Distributor: MountImage |
| Available From: www.mountImage.com |
| Description: MountImage Pro is a simple tool to present a forensic duplicate as a volume and hard drive attached to the computer. This approach to accessing a forensic duplicate can be useful for running tools that cannot process a forensic duplicate directly and require a mounted file system. |
 |
| Name: IMDisk |
| Page Reference: 159 |
| Author/Distributor: LTR Data |
| Available From: http://www.ltr-data.se/opencode.html/#ImDisk |
| Description: This simple free utility for Windows computers to mount a forensic duplicate as a virtual drive letter. The following command options effectively mount a forensic duplicate read-only on drive letter W: C:\Windows\system32>imdisk -a -o ro -f E:\Forensics\image-001.dd -s 1 30000K -m W: Creating device... Created device 1: W: -> E:\Forensics\image-001.dd Notifying applications... Done. The following command options unmount a forensic duplicate read-only on drive letter W: C:\Windows\system32>imdisk -d -m W: Notifying applications... Flushing file buffers... Locking volume... Dismounting filesystem... Removing device... Removing mountpoint... Done. |
|
| Forensic Examination of Windows Systems |
|
| Name: FTK |
| Page Reference: 175 |
| Author/Distributor: AccessData |
| Available From: http://www.accessdata.com |
| Description: FTK is a commercial integrated digital forensic examination program that has a wide range of features for examining forensic duplicates of storage media. The most basic use of FTK is to perform forensic examinations of file systems as shown in the following figure. In addition to parsing and displaying common file systems, FTK recovers deleted files, performs indexing to facilitate keyword searching, and interprets specific file formats in order to extract additional information. |
 |
| Name: Encase |
| Page Reference: 175 |
| Author/Distributor: Guidance Software |
| Available From: http://www.guidancesoftware.com |
| Description: EnCase is a commercial integrated digital forensic examination program that has a wide range of features for examining forensic duplicates of storage media. The most basic use of EnCase is to perform forensic examinations of file systems as shown in the following figure. In addition to parsing and displaying common file systems, EnCase recovers deleted files, can perform keyword searching, interprets specific file formats in order to extract additional information, and has a scripting language that can be used to add customized functionality and automate routine tasks. |
 |
| Name: ProDiscover |
| Page Reference: 175 |
| Author/Distributor: Technology Pathways |
| Available From: http://www.techpathways.com |
| Description: As with other integrated digital forensic examination programs, ProDiscover has the ability to parse and display file systems and other data structures on Windows systems, including Registry, Event Log and Shadow Volume data. The following screenshot shows ProDiscover being used to explore the contents of clusters. |
 |
| Name: The Sleuth Kit & Autopsy |
| Page Reference: 175 |
| Author/Distributor: Brian Carrier and Open Source Collaborators |
| Available From: http://www.sleuthkit.org |
| Description: The Sleuthkit (TSK) is a free open source package of command line utilities for conducting forensic examination of file systems. Although TSK is designed to run on UNIX/Linux systems, it can used to examine FAT, NTFS, and HFS+ file systems. These utilities include fls to list files and directories in the file system and display associated metadata. In addition, a simple Web-based be graphical user interface called Autopsy is provided to facilitate use of TSK utilities. |
 |
| Name: X-ways |
| Page Reference: 175 |
| Author/Distributor: WinHex |
| Available From: http://www.x-ways.com |
| Description: X-Ways is a commercial program for performing forensic examination of storage media and files. The most basic use of X-Ways is to perform forensic examinations of file systems as shown in the figure below. In addition, X-Ways can be used to recovered deleted files and perform keyword searches. |
 |
| Timeline Generation |
| Name: Log2Timeline |
| Page Reference: 166 |
| Author/Distributor: Kristinn Gudjonsson |
| Available From: http://www.log2timeline.net/ |
| Description: Log2Timeline is a free, open source tool that extracts information from a variety of logs and other date-time stamped data sources and consolidates the information into a comprehensive timeline for review. |
| Forensic Examination of Common Sources of Information on Windows Systems Co |
| Name: WinPreFetchView |
| Page Reference: 163 |
| Author/Distributor: NirSoft |
| Available From: http://www.nirsoft.net/utils/win_prefetch_view.html |
| Description: WinPreFetch is a tool for extracting details from PreFetch files including the first time an executable was run, the last time it was run, and the number of times it was run as shown here. |
 |
| Name: Prefetch Parser |
| Page Reference: 163 |
| Author/Distributor: Redwolf |
| Available From: http://redwolfcomputerforensics.com/downloads/parse_prefetch_info_v1.4.zip |
| Description: PreFetchParser is a program that extracts information from Prefetch files and outputs the results in a simple format for examination. The following screenshots show Pretch file being extracted in HTML report format. |
 |
 |
| Name: Autoruns |
| Page Reference: 165 |
| Author/Distributor: Microsoft |
| Available From: http://technet.microsoft.com/en-us/sysinternals/bb963902 |
| Description: Autoruns is a program that can run against a live system or a forensic duplicate to extract details from various locations that will launch programs when a Windows computer starts up. In addition to providing a categorized interface to this information, Autoruns can be useful for identifying unusual startup entries. For example, Autoruns can show executables that have not been signed, which may be an indication of malware. As another example, Autoruns can reveal startup entries that are missing the associated executable on the disk as shown in the following figure, which may be an indication of malicious activity or be a reference to malware that was deleted by AntiVirus software: |
 |
| Name: Log Parser |
| Page Reference: 166 |
| Author/Distributor: Microsoft |
| Available From: http://www.microsoft.com/downloads/en/details.aspx?FamilyID=890cd06b-abf8-4c25-91b2-f8d975cf8c07 |
| Description: LogParser is a versatile utility for parsing common types of data on Microsoft Windows systems, including file system entries, Registry entries, Event logs and IIS Web server logs. In addition to simply parsing files, LogParser provides a SQL query interface to the support file formats that can be useful for extracting specific information. For example, the following use of LogParser extracts all logon records from a Windows Security Event log and displays a list of usernames and the date and time they were used to log onto the system. C:\>LogParser "SELECT TimeGenerated AS LogonDate, EXTRACT_TOKEN(Strings, 0, '|') AS Username FROM 'SecEvent.Evt' WHERE EventID NOT IN (541;542;543) AND EventType = 8 AND EventCategory = 2 AND Username NOT LIKE 'IUSR_%'“ LogonDate Username ------------------- ------------- 2002-05-06 21:03:31 esmith 2002-05-09 17:42:06 adoe 2002-05-09 19:56:53 esmith 2002-05-12 00:12:32 esmith |
| Name: Event Log Explorer |
| Page Reference: 166 |
| Author/Distributor: FSPro Labs |
| Available From: http://www.eventlogxp.com/ |
| Description: Event Log Explorer is a useful program for examining Windows Event Logs. This tool can be used to filter on specific events as shown in the following figure, enabling forensic examiners to focus on a subset of events that may be relevant to a malware incident. In additon, Event Log Explorer supports keyword searching of Event log entries, which can be useful for finding specific events related to malware incidents. |
 |
| Name: Registry Viewer |
| Page Reference: 171 |
| Author/Distributor: AccessData |
| Available From: http://www.accessdata.com |
| Description: Registry Viewer is a program for examining Registry hives from Windows systems. This program displays Registry values and associated data, and has the ability to decode certain values that would otherwise be obfuscated. Registry Viewer also has features for filtering specific Registry keys and performing keyword searches. In addition, Registry Viewer has a feature for finding all alterations in a Registry hive within a specific date range as shown in the following figure. |
 |
| Name: RegRipper |
| Page Reference: 170-171 |
| Author/Distributor: Harlan Carvey |
| Available From: http://regripper.wordpress.com/regripper/ |
| Description: Registry Ripper (aka RegRipper) is a utility for extracting specific information from Windows Registry hives. This tool uses plug-in files to specify which items will be extracted from Registry hives. These plug-ins can be run against a suitable Registry hive from a command line or using the Registry Ripper graphical user interface shown here for a System Registry hive. |
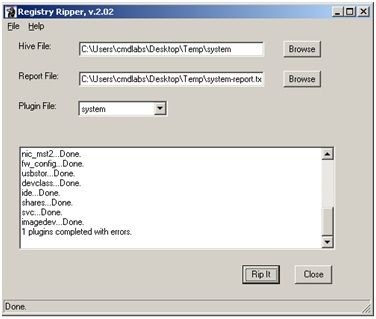 |
| Name: Registry Decoder |
| Page Reference: 170-171 |
| Author/Distributor: Digital Forensic Solutions |
| Available From: http://www.digitalforensicssolutions.com |
| Description: Registry Decoder is a free, open source tool for examining Windows Registry hives, extracting specific information using plug-ins, and can present the results in a report. This tool has the added functionality of comparing two different versions of a Registry hive and showing the differences. In addition, Registry Decoder supports keyword searching within a specified timeframe. |
 |
 |
| Name: NetAnalysis |
| Page Reference: 169 |
| Author/Distributor: Digital Detective Group |
| Available From: http://www.digital-detective.co.uk/ |
| Description: NetAnalyzer extracts information from a wide variety of Web browsers, including Internet Explorer, Firefox, Safari, Mozilla, Google Chrome, Orca, Flock, Yahoo!, AOL ARL files, and other file types. This tools processes and displays browsing history, cookies, and cache data with associated date/time stamps. NetAnalyzer also has features for filtering specific entries and performing keyword searches. |
 |
| Name: Restore Point Analyzer |
| Page Reference: 171 |
| Author/Distributor: Mandiant |
| Available From: http://www.mandiant.com/resources/download/research-mandiant-restore-point-analyzer |
| Description: The Restore Point Analyzer utility processes the change.log in Windows Restore Points to provide a list of files that were included in the restore point. |
 |
| Name: Web Historian |
| Page Reference: 169 |
| Author/Distributor: Mandiant |
| Available From: http://www.mandiant.com/resources/download/web-historian |
| Description: Mandiant Web Historian extracts browsing history associated with several Web browsers (Firefox 2, Firefox 3+, Chrome 3+, Internet Explorer 5−8, Safari 3+). This tool processes history, temporary cache data and cookies with associated date-time stamps. However, it presents this information in separate tabs as shown here. |
| Name: Gargoyle |
| Page Reference: 169 |
| Author/Distributor: Wetstone |
| Available From: http://wetstonetech.com/cgi-bin/shop.cgi?view,2 |
|
Description: Gargoyle is a tool for scanning file systems for artifacts of known malware as shown here. |
 |
