Chapter 5 File Identification and Profiling
| Capturing File Appearance |
| Name: Shutter |
| Page Reference: 260 |
| Author/Distributor: Mario Kemper |
| Available From: http://shutter-project.org/ |
Description: An open source feature-rich graphical tool for screen captures. Shutter enables the user to capture a select area, window, entire desktop, and even a target web site. In addition to capture capabilities, Shutter has a built-in drawing feature and numerous plugins to manipulate the screen capture. |
| Command-line Hashing Utilities |
| Name: MD5sum | ||||||||||||||||
|
Page Reference: 262 |
||||||||||||||||
|
Author/Distributor: Jesse Kornblum |
||||||||||||||||
|
Available From: http://md5deep.sourceforge.net/ |
||||||||||||||||
|
Description: A suite of utilities to compute the message digests (MD5, SHA-1, SHA-256, Tiger, or Whirlpool) of files. md5deep offers a number of powerful functions, including recursive hashing, hash comparison mode, time estimation, and piecewise hashing, among others. |
||||||||||||||||
Helpful Switches:
|
| GUI Hashing Utilities |
| Name: GUIMD5Sum (qtmd5summer) |
| Page Reference: 262 |
| Author/Distributor: irfanhab |
| Available From: http://qtmd5summer.sourceforge.net |
Description: A graphical utility for calculating the MD5 hash value of directories, sub-directories, and individual files. GUIMD5sum offers a clean and simple interface for simple processing of multiple files. |
| Name: Parano |
| Page Reference: 263 |
| Author/Distributor: BerliOS |
| Available From: http://parano.berlios.de |
Description: Gnome utility for creating, verifying, and managing hash files. Currently, Parano supports MD5, SHA-1 and (Simple File Verification) SFV. |
| File Similarity Indexing |
| Name: SSDeep |
||||||||||||||||||||||
| Page Reference: 264 | ||||||||||||||||||||||
| Author/Distributor: Jesse Kornblum | ||||||||||||||||||||||
| Available From: http://ssdeep.sourceforge.net/ | ||||||||||||||||||||||
| Description: A fuzzy hashing tool that computes a series of randomly sized checksums for a file, allowing file association between files that are similar in file content but not identical. | ||||||||||||||||||||||
Helpful Switches:
|
| Name: DeepToad |
| Page Reference: 264 |
| Author/Distributor: Joxean Koret |
| Available From: http://code.google.com/p/deeptoad/ |
Description: Inspired by ssdeep, Deeptoad (python) is a tool to clusterize similar files using fuzzy hashing techniques. The menu and tool is usage is shown below: |
| File Visualization |
| Name: Crypto Visualizer (part of the Crypto Implementation Analysis Toolkit) |
| Page Reference: 304 |
| Author/Distributor: Omar Herrera |
| Available From: http://sourceforge.net/projects/ciat/ |
| Description: The Crypto Implementations Analysis Toolkit is a suite of tools for the detection and analysis of encrypted byte sequences in files. CryptoVisualizer displays the data contents of a target file in a graphical histogram, allowing the digital investigator to identify pattern or content anomalies.  |
| Name: BinVis | ||||||||||||||||||
|
Page Reference: 266 |
||||||||||||||||||
|
Author/Distributor: Gregory Conti/Marius Ciepluch |
||||||||||||||||||
|
Available From: http://code.google.com/p/binvis/ |
||||||||||||||||||
|
Description: BinVis is binary file visualization framework, that enables the digital investigator to view binary structures in unique ways. As of this writing, the tool does not natively install and run in Linux; WINE or CrossOver must first be installed on the analysis system. As shown in the figure below, BinVis provides for eight distinct visualization modes that render alternative graphical perspectives on the target file structure, data patterns and contents. Particularly useful for analysis is the interconnectedness of the views; for example if digital investigator opens the byteplot diaply and strings viewer, with each region that is clicked on in the byteplot viewer the same area of the target file is automatically displayed in the strings viewer. 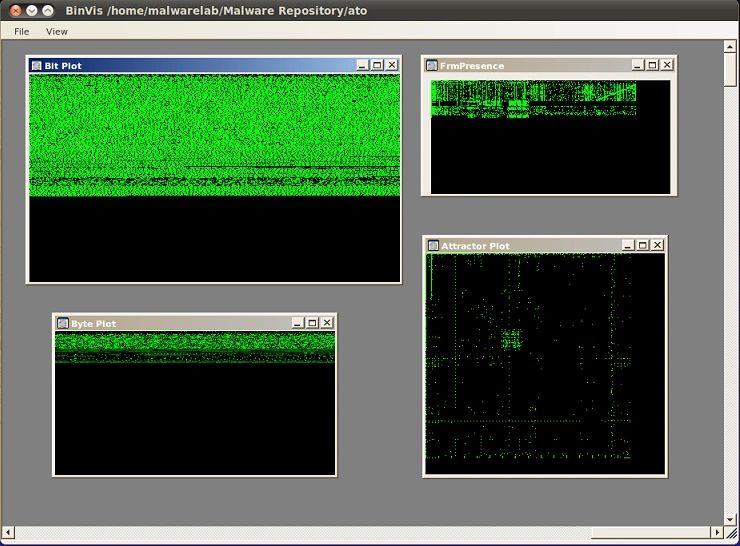
|
| Hexadecimal Editors |
| Name: Okteta |
| Page Reference: 268 |
| Author/Distributor: Okteta |
| Available From: http://www.ohloh.net/p/okteta |
|
Description: A robust GUI hex editor for analyzing raw data files. Multifunctional, Okteta has a number of valuable file analysis modules—such as checksum calculator, string extraction, structure analysis, decoding, and statistical tools—that can be viewed or minimized from the main interface. |
| Antivirus |
|
Name: Avast |
||||||||
| Page Reference: 272 | ||||||||
|
Author/Distributor: Avast |
||||||||
|
Available From: http://files.avast.com/files/linux/avast4workstation-1.3.0-1.i586.rpm; http://files.avast.com/files/linux/avast4workstation_1.3.0-2_i386.deb; http://files.avast.com/files/linux/avast4workstation-1.3.0.tar.gz |
||||||||
|
Description: A command-line and graphical anti-virus solution for on-access scans. |
||||||||
Helpful Switches:
|
| Name: Avira (for Linux) | ||||||||||||||||
|
Page Reference: 272 |
||||||||||||||||
|
Author/Distributor: Avira Antivirus |
||||||||||||||||
| Available From: http://dl1.avgate.net/down/unix/packages/antivir-workstation-pers.tar.gz | ||||||||||||||||
|
Description: A free command-line anti-virus solution that can perform on-demand and on-access scans. |
||||||||||||||||
Helpful Switches:
|
| Name: AVG (for Linux) |
||||||||||||||||||||
| Page Reference: 272 | ||||||||||||||||||||
| Author/Distributor: AVG |
||||||||||||||||||||
| Available From: http://free.avg.com/us-en/download.prd-alf |
||||||||||||||||||||
| Description: A free command-line anti-virus solution that can perform on-demand and on-access scans. |
||||||||||||||||||||
|
Helpful Switches:
|
| Name: Comodo (for Linux) |
|
Page Reference: 272 |
|
Author/Distributor: Comodo |
|
Available From: http://www.comodo.com/home/download/download.php?prod=antivirus-for-linux |
Description: A free command-line and graphical anti-virus solution. |
| Name: ClamAV | ||||||||||||
| Page Reference: 272 |
||||||||||||
| Author/Distributor: The Clam Team |
||||||||||||
| Available From: http://www.clamav.net/lang/en/ |
||||||||||||
| Description: A free command-line anti-virus solution that can perform on-demand and on-access scans. A GUI overlay, ClamTK is available through most Linux distribution package managers. | ||||||||||||
Helpful Switches:
|
|
Name: F-Prot (for Linux) |
||||||||||||||||||
| Page Reference: 272 | ||||||||||||||||||
|
Author/Distributor: Commtouch |
||||||||||||||||||
|
Available From: http://www.f-prot.com/products/home_use/linux/; http://www.f-prot.com/download/home_user/download_fplinux.html |
||||||||||||||||||
|
Description: A free command-line anti-virus solution that can perform on-demand and on-event scans. |
||||||||||||||||||
Helpful Switches:
|
|
Name: BitDefender (for Linux) |
||||||||||||||
| Page Reference: 272 | ||||||||||||||
|
Author/Distributor: Bitdefender |
||||||||||||||
|
Available From: http://unices.bitdefender.com/downloads/ |
||||||||||||||
|
Description: A free command-line and GUI anti-virus solution that can perform on-demand and on-access scans. |
||||||||||||||
Helpful Switches:
|
| Name: Panda (for Linux) |
| Page Reference: 272 |
| Author/Distributor: Panda Security |
| Available From: http://research.pandasecurity.com/free-commandline-scanner/ |
| Description: A free command-line anti-virus solution that can perform on-demand and on-event scans. |
| Embedded Artifact Extraction |
| Strings |
| Name: Strings | ||||||||
| Page Reference: 272 | ||||||||
|
Author/Distributor: GNU |
||||||||
|
Available From: GNU Binary Utilities (binutils); Native to Linux distributions |
||||||||
|
Description: Displays plain-text ACSII and UNICODE (contiguous) characters within a file. |
||||||||
Helpful Switches:
|
| File Dependencies |
| Name: LDD | ||||||||||
| Page Reference: 281 | ||||||||||
| Author/Distributor: Rowland McGrath and Ulrich Drepper |
||||||||||
| Available From: Native to Linux distributions |
||||||||||
| Description: Displays the shared libraries required by a target program/executable file. Standard usage: $ldd <target file> |
||||||||||
Helpful Switches:
|
| Name: ELF Library Viewer |
| Page Reference: 283 |
| Author/Distributor: Michael Payne |
| Available From: http://www.purinchu.net/software/elflibviewer.php |
| Description: Graphical utility for displaying library dependencies of a target ELF file. Libraries are displayed in hierarchial order with respective file path prominently displayed in a separate field. A built- in search tool enables the digital investigator to quickly query and locate specific libraries—identified files are displayed in red text. 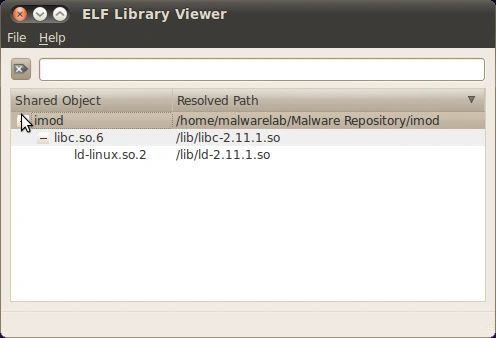 |
| Name: Visual Dependency Walker |
| Page Reference: 283-284 |
| Author/Distributor: Filippos Papadopoulos and David Sansome |
| Available From: http://freecode.com/projects/visual_ldd |
|
Description: Graphical utility for displaying library dependencies of a target ELF file. Libraries are |
| Name: DepSpec |
| Page Reference: 284 |
| Author/Distributor: Kyle McFarland |
| Available From: https://launchpad.net/depspec |
|
Description: A dual-paned GUI for file dependency analysis that reveals imports libraries, exported
|
| Name: ELF Dependency Walker |
| Page Reference: 283-284 |
| Author/Distributor: Peter Cheung |
| Available From: http://code.google.com/p/elf-dependency-walker/ |
Description: A feature-rich ELF file dependency analysis tool that provides alternative viewing options. In tree mode, suspect files are displayed in hierarchical tree order, with dependencies viewable by expanding the tree. Upon selecting a target file or dependency, the file structure is displayed in the right-hand viewing pane. Alternatively, the graph mode enables the digital investigator to render the file dependencies of a target file specimen into eight different graphical layouts for contrasting perspective. Graphical layouts can be saved as a Portable Network Graphics (.png) image file. |
| Extracting Symbolic and Debug References |
| Name: NM | ||||||||||||||||
| Page Reference: 285 |
||||||||||||||||
| Author/Distributor: GNU |
||||||||||||||||
| Available From: GNU Binary Utilities (binutils); Native to Linux distributions |
||||||||||||||||
| Description: Command-line utility that lists symbols in a target file. |
||||||||||||||||
Helpful Switches:
|
| Name: Gedit Symbol Browser Plugin |
| Page Reference: 291 |
| Author/Distributor: Micah Carrick |
| Available From: http://www.micahcarrick.com/gedit-symbol-browser-plugin.html |
Description: A graphical symbol extraction and analysis tool that is leveraged as a plugin through gedit.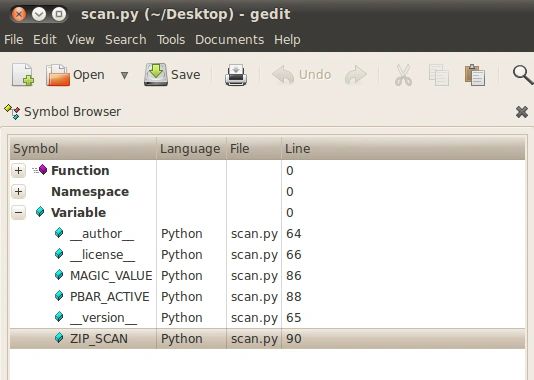 |
| File Metadata |
|
Name: Exiftool |
||||||||||||
| Page Reference: 294 | ||||||||||||
| Author/Distributor: Phil Harvey | ||||||||||||
| Available From: http://www.sno.phy.queensu.ca/~phil/exiftool/ | ||||||||||||
|
Description: A powerful command-line metadata extraction tool that can acquire meta information from ELF, PDF, MS Office, among other types of target malware files. |
||||||||||||
Helpful Switches:
|
| ELF File Analysis |
| Name: Binutils |
| Page Reference: 276 |
| Author/Distributor: GNU |
| Available From: www.gnu.org/software/binutils |
| Description: A collection of binary tools for manipulating and analyzing object and archive files, including, among others, nm (list symbols from object files); strings, readelf, and objdump. |
| Name: Elfutils | ||||||||||||||||
| Page Reference: 276 | ||||||||||||||||
|
Author/Distributor: Ulrich Drepper |
||||||||||||||||
| Available From: https://fedorahosted.org/elfutils/ | ||||||||||||||||
Description: A collection of utilities for working with ELF object files, including:
|
| Name: Greadelf |
| Page Reference: 276 |
| Author/Distributor: Ashok Das |
| Available From: https://code.google.com/p/greadelf/ |
| Description: GUI for the readelf and eu-readelf utilities that provides an easy-to-navigate multi- pane views of ELF file structures and contents. 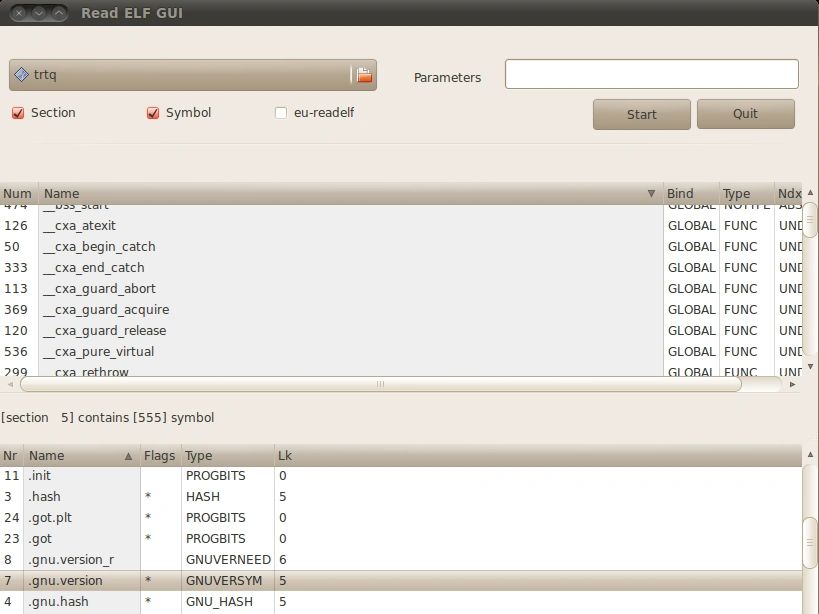 |
| Name: ERESI Reverse Engineering Software Interface ("ERESI") |
| Page Reference: 308 |
| Author/Distributor: Julien Vanegue and the ERESI team |
| Available From: http://www.eresi-project.org/ |
| Description: A framework of multi-architecture binary analysis tools geared toward reverse engineering and program manipulation. The framework includes the following tools: elsh, kernsh, e2dbg, etrace, evarista, kedbg. In addition to these programs ERESI contains numerous specialized libraries that can be used by ERESI and/or in third-party programs. |
| Name: Readelf |
||||||||||||||||||||||
| Page Reference: 277, 305, 308 |
||||||||||||||||||||||
| Author/Distributor: GNU | ||||||||||||||||||||||
| Available From: www.gnu.org/software/binutils |
||||||||||||||||||||||
| Description: A command line tool that diplays the structure and contents of ELF files. |
||||||||||||||||||||||
|
Helpful Switches:
|
| Malicious Document Analysis |
| Malicious Document Analysis: PDF Files |
|
Name: Origami |
||||||||||||
|
Page Reference: 341-344 |
||||||||||||
|
Author/Distributor: Gillaume Delugré, Frédéric Raynal (Contributor) |
||||||||||||
|
Available From: http://esec-lab.sogeti.com/dotclear/index.php?pages/Origami; http://code.google.com/p/origami-pdf/ |
||||||||||||
|
Description: Origami is a framework of tools written in Ruby designed to parse and analyze malicious PDF documents as well as to generate malicious PDF documents for research purposes. Origami contains a series of Ruby parsers—or core scripts (described in the table below), scripts, and Walker (a GTK GUI interface to examine suspect PDF files, depicted in the Figure below).  |
||||||||||||
Helpful Switches:
|
| Name: Jsunpack-n | |
| Page Reference: 344 | |
| Author/Distributor: Blake Hartstein |
|
| Available From: https://code.google.com/p/jsunpack-n/; Jsunpack: http://jsunpack.jeek.org/dec/go |
|
Description: Jsunpack-n, "a generic JavaScript unpacker," is a suite of tools written in python designed to emulate browser functionality when navigating to URLs. Although a powerful tool for researchers to identify client-side browser vulnerabilities and exploits, Jsunpack-n is also a favorite tool of digital investigators to examine suspect PDF files and extract embedded Javascript. In the figure below, the pdf.py script is used to extract JavaScript from a suspect PDF file specimen and write it to a separate file for further analysis.
|
| Name: PDFMiner |
| Page Reference: 347 |
| Author/Distributor: Yusuke Shinyama |
| Available From: http://www.unixuser.org/~euske/python/pdfminer/index.html |
| Description: Python PDF parser and analyzer. PDF Miner consists of numerous python scripts to examine the textual data inside of a PDF file, including pdf2txt.py (extracts text contents from a PDF file) and dumppdf.py (dumps the internal contents of a PDF file in pseudo-XML format). |
| Name: Peepdf | ||||||||||||||||||||
| Page Reference: 347 | ||||||||||||||||||||
|
Author/Distributor: Jose Miguel Esparza |
||||||||||||||||||||
| Available From: http://code.google.com/p/peepdf/ | ||||||||||||||||||||
Description: Command-line based PDF parser and analyzer. Peepdf can be invoked from the command line and pointed toward a target file (shown in the figure below), or set into ”interactive mode,” (using the –i switch) creating a peepdf ”PPDF shell” wherein commands can be directly queried. |
||||||||||||||||||||
Helpful Switches:
|
| Name: Malzilla |
| Page Reference: 351 |
| Author/Distributor: Boban Spasic aka bobby |
| Available From: http://malzilla.sourceforge.net/downloads.html |
| Description: Described by the developer as a malware hunting tool, Malzilla is commonly used by malicious code researchers to navigate to potentially malicious URLs in an effort to probe the contents formalicious code and related artifacts. However, Malzilla has a variety of valuable decoding and shellcode analysis features making it an essential tool in the digital investigator’s arsenal for exploring malicious PDF files. As of this writing, the tool does not natively install and run in Linux; WINE or CrossOver must first be installed on the analysis system.  |
| Name: Hachoir-urwid |
| Page Reference: 357 |
| Author/Distributor: Victor Stinner |
| Available From: https://bitbucket.org/haypo/hachoir/wiki/hachoir-urwid |
Description: Based upon the hachoir-parser, the hachoir-urwid is a binary file exploration utility that can parse a myriad of file types, including OLE files.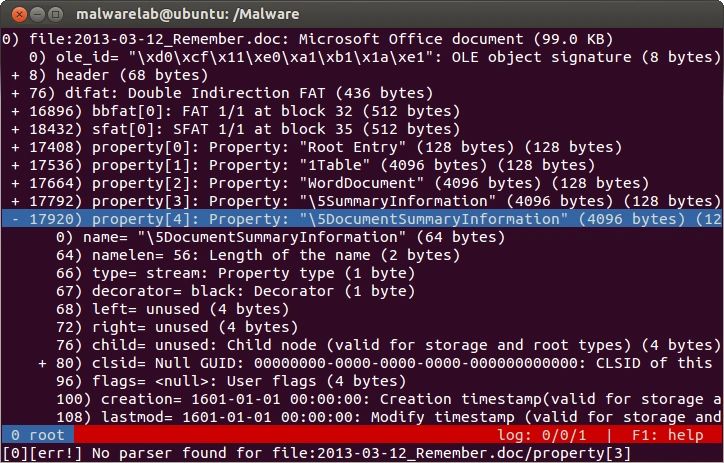 |
| Name: Hachoir-wx |
| Page Reference: 271, 357 |
| Author/Distributor: Victor Stinner |
| Available From: https://bitbucket.org/haypo/hachoir/wiki/hachoir-wx |
| Description: A wxWidgets-based GUI for Hachoir that enables the digital investigator to parse binary files, including OLE files. 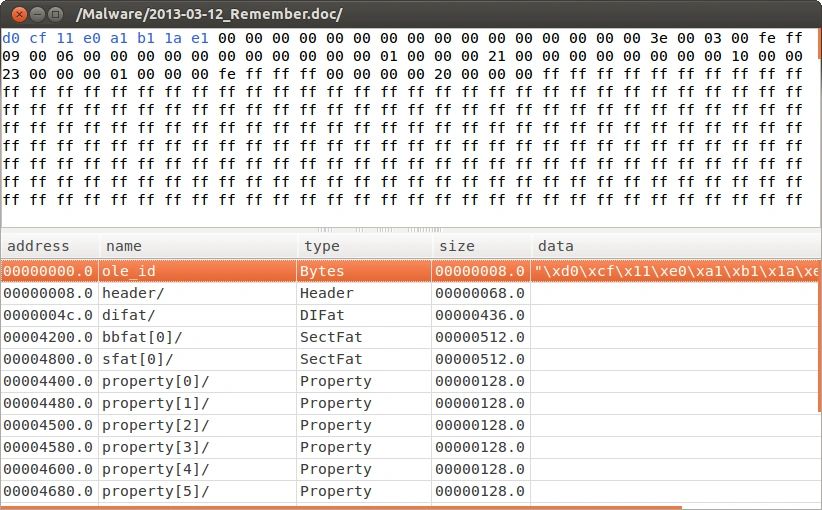 |
| Name: pyOLEScanner | |
| Page Reference: 357 |
|
| Author/Distributor: Giuseppe ’Evilcry’ Bonfa |
|
| Available From: https://github.com/Evilcry/PythonScripts |
|
| Description: Python script for triaging OLE files for indicators of malice, including embedded executables, API references, shellcode, Macros and other artifacts.
|
| Name: Beye (Binary Eye) (formerly known as Binary vIEWer, "BIEW") |
| Page Reference: 357 |
| Author/Distributor: Nickols Kurshev |
| Available From: http://beye.sourceforge.net/ |
Description: A terminal user interface based tool for parsing numerous binary file formats, including ELF and OLE files. |
| Name: Structured Storage Viewer |
| Page Reference: 357 |
| Author/Distributor: MiTec/Michal Mutl |
| Available From: http://www.mitec.cz/ssv.html |
| Description: GUI tool for analyzing and manipulating MS OLE Structured Storage files. As of this writing, the tool does not natively install and run in Linux; WINE or CrossOver must first be installed on the analysis system. 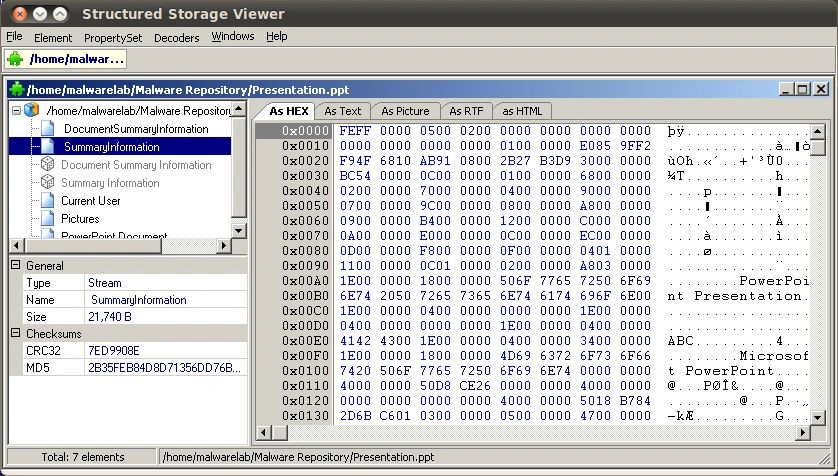 |



